Writen by
Mr Robot is wrong, he is not in control
Article
A few days ago I started watching Mr robot for fun. And I pause just after the first scene. 📹
For those who do not remember:
And a question, me trigger, what does Elliot say?
"Who controls the exit node is in control of traffic"
In this case I agree with him the Tor protocol can be compared to a proxy string where http traffic can be spied by the exit node. 🧅 With some research i could find some interesting "problem" on this point:
SSLstrip
With some research and tests on my side, I was able to make a more precise conclusion, the ssl is not secure as we think in this case. We can do what is called "sslstrip" and thus we have ruined the whole chain and all the user’s traffic. Interesting doc on this point:
- https://nopsec.com/blog/responder-beyond-wpad/
- https://security.stackexchange.com/questions/8145/does-apfte-prevent-man-in-the-middle-attacks-by-proxy-server
- https://loadbalancer.org/blog/transparent-vs-explicit-proxy-which-method-should-i-use/
- https://9proxy.com/blog/transparent-proxy-vs-explicit-proxy
- https://github.com/moxie0/sslstrip
- https://github.com/droe/sslsplit
- https://youtu.be/X5oXcXrQDqE?feature=shared
Ron’s architecture
Ok now let’s go back to a fundamental problem of tor, only one server can use a configuration file of the website tor (or I missed an update of tor maybe?). So in this case I drew a logical architecture of the infrastructure of the Ron with 2 mirrors that each manage 50% of the traffic (for example)
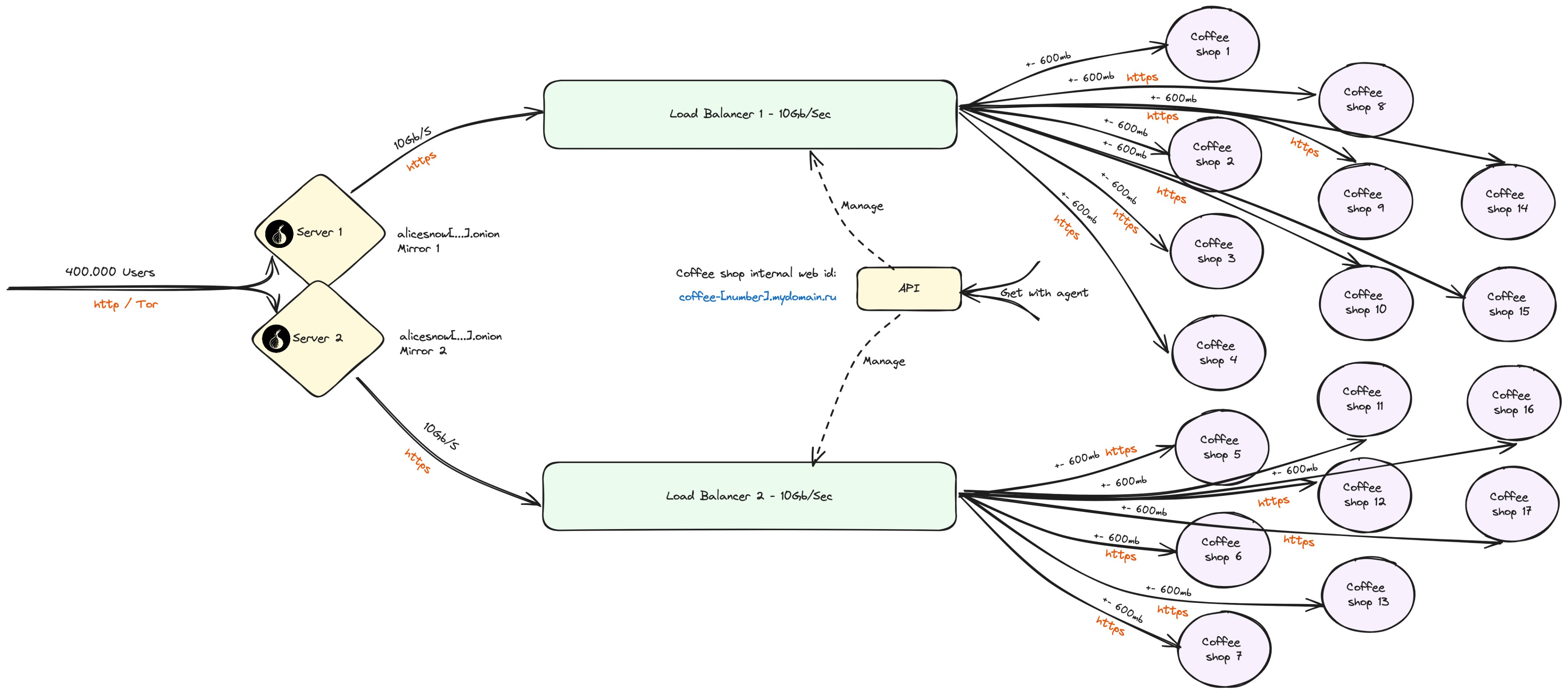
Note: this architecture has been realized in the case where it is considered that the number of users is equally distributed on both servers. In addition, we must also consider that each coffee shop has an equivalent server with regard to performance.
Let's get back to the video. With some logic, what he said is quite "strange". Let’s be Elliot a little bit and try to understand his plan:
- The Wifi is fast (nothing is free)
- Scan the local area (with nmap orrustscan)
- Find the server on the network (wtf is this ? lol)
- Hack the server and find Ron’s website. (fake news: see what he says)
So the question is, what’s Elliot’s real plan?
Ron’s cloned architecture
In the case of Ron having the same network system as my schema, hacking the tor control system is not interesting, because the tor site is not on the same server. So the only way to hack the tor website is to hack the server before the load balancer.
Next, with this problem, how did he know the mirror .onion url? I’m not sure that a "header hacking" is possible in this case. So the only way to know the mirror URL is to hack the server before load balancer and find it in configuration file or source code.
So, in my case, to say that the tor network is THE vulnerable point is not correct. The real vulnerability is the server hosted in the cafe, and then the tor network for deeper access.
But wait...
if he has access to the server, why didn’t he just scan the servers themselves and find the tor website data? And do not waste time with the exploit of exit node of the network tor?
Exploiting a server directly is often easier than hacking Tor through an exit node exploit because, with server access, attackers can directly target vulnerabilities like weak credentials, outdated software, or misconfigurations, allowing them to quickly access sensitive data or system controls. In contrast, hacking Tor via exit nodes requires intercepting or manipulating traffic within a highly anonymized and encrypted network, which is much more complex and offers fewer opportunities for directly accessing or de-anonymizing the hidden service itself.
Conclusion
I hope my explanation is clear, and I hope I haven’t missed a point in this example, but I’m quite sure that this scene doesn’t show the real exploitable point of the system.